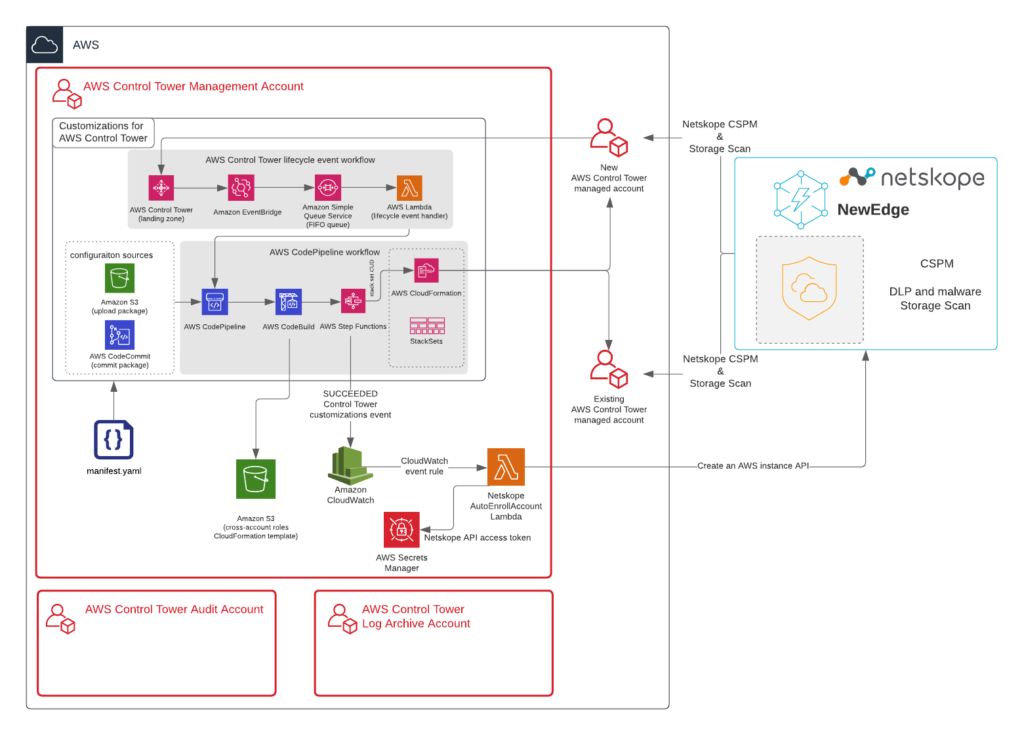
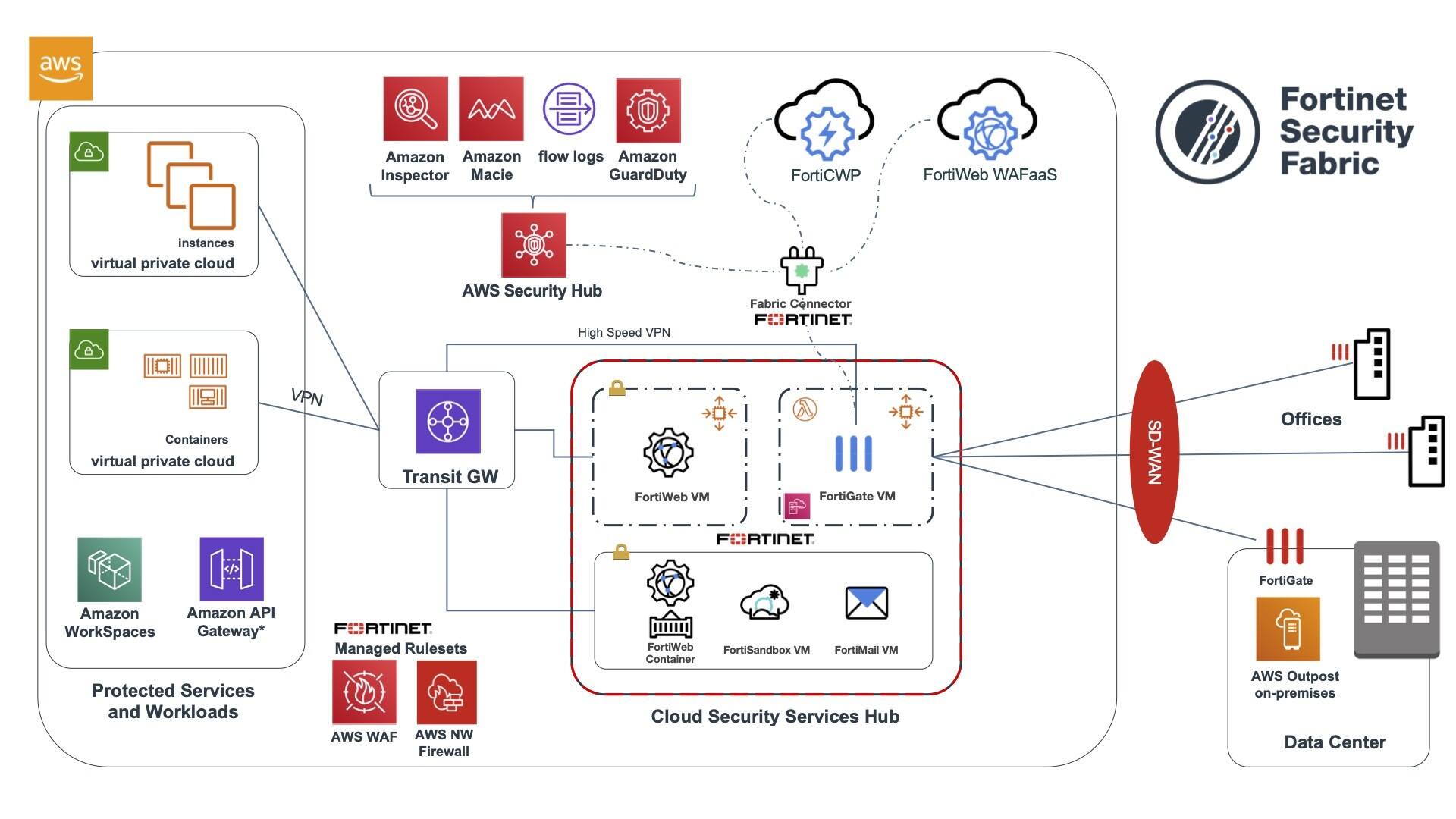
How to build a CI/CD pipeline for container vulnerability scanning with Trivy and AWS Security Hub | AWS Security Blog
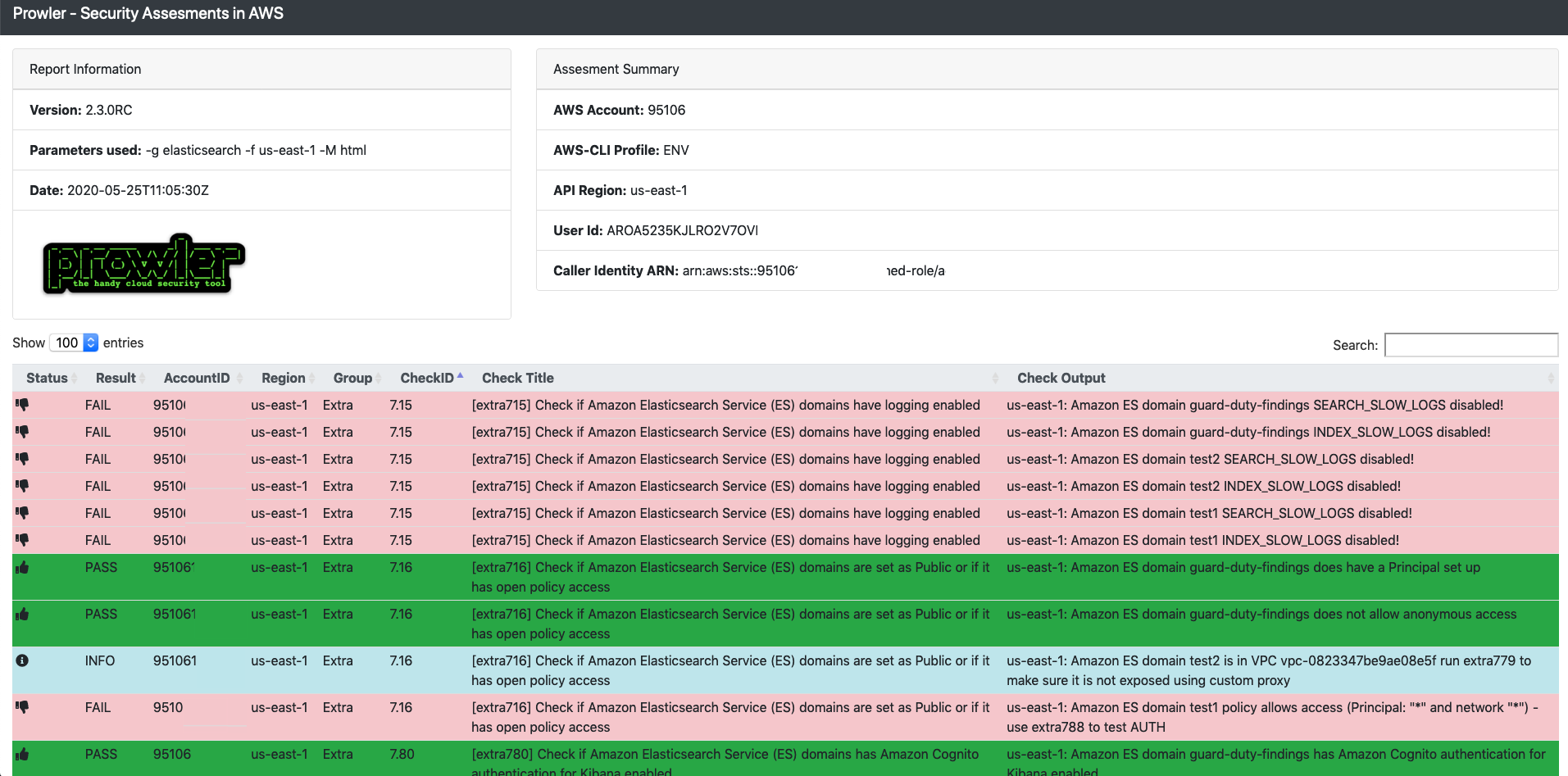
Top Security Scanning and Vulnerability Management Tools |AWS| | by Kubernetes Advocate | AVM Consulting Blog | Medium

Top Security Scanning and Vulnerability Management Tools |AWS| | by Kubernetes Advocate | AVM Consulting Blog | Medium

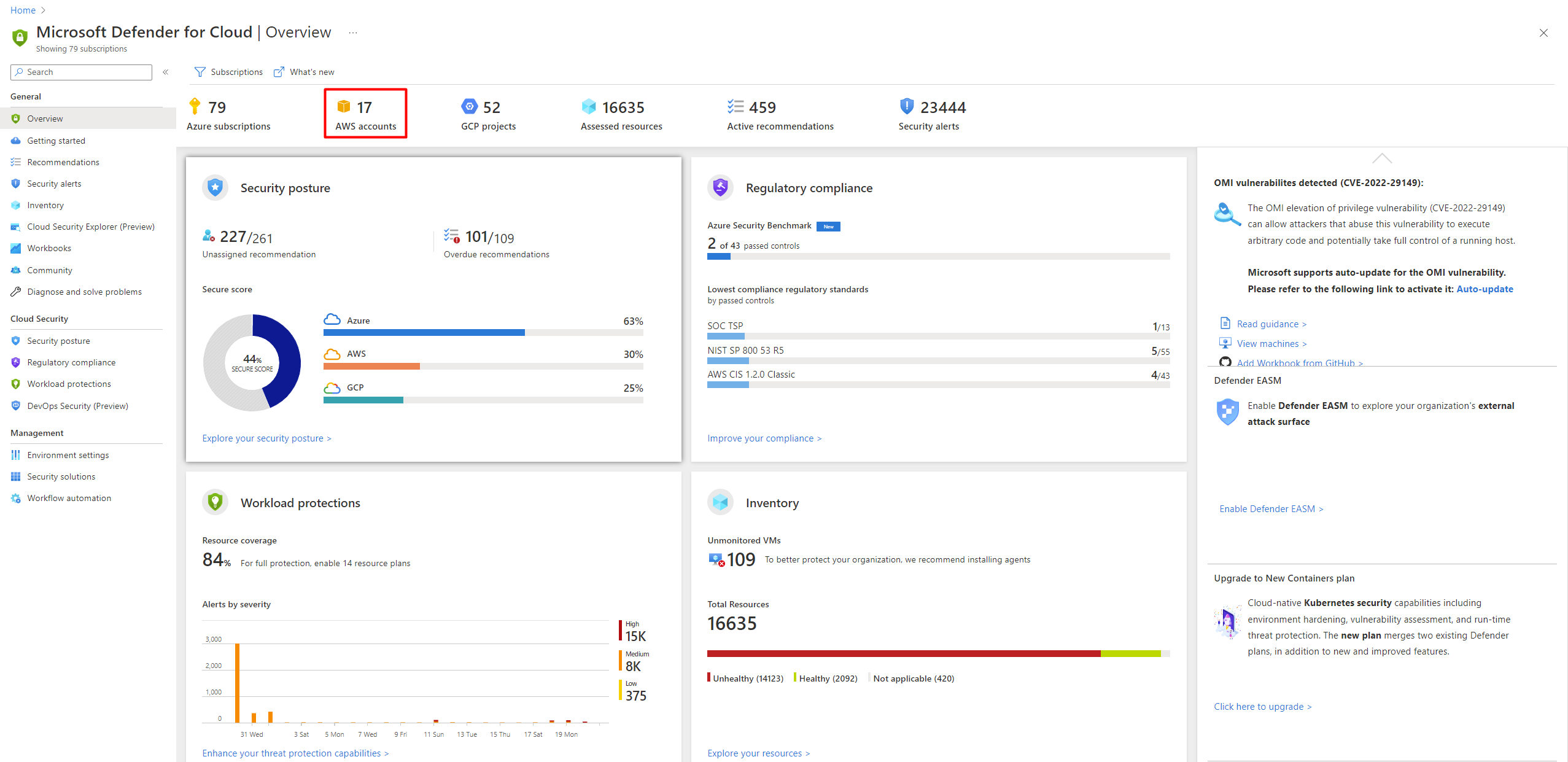
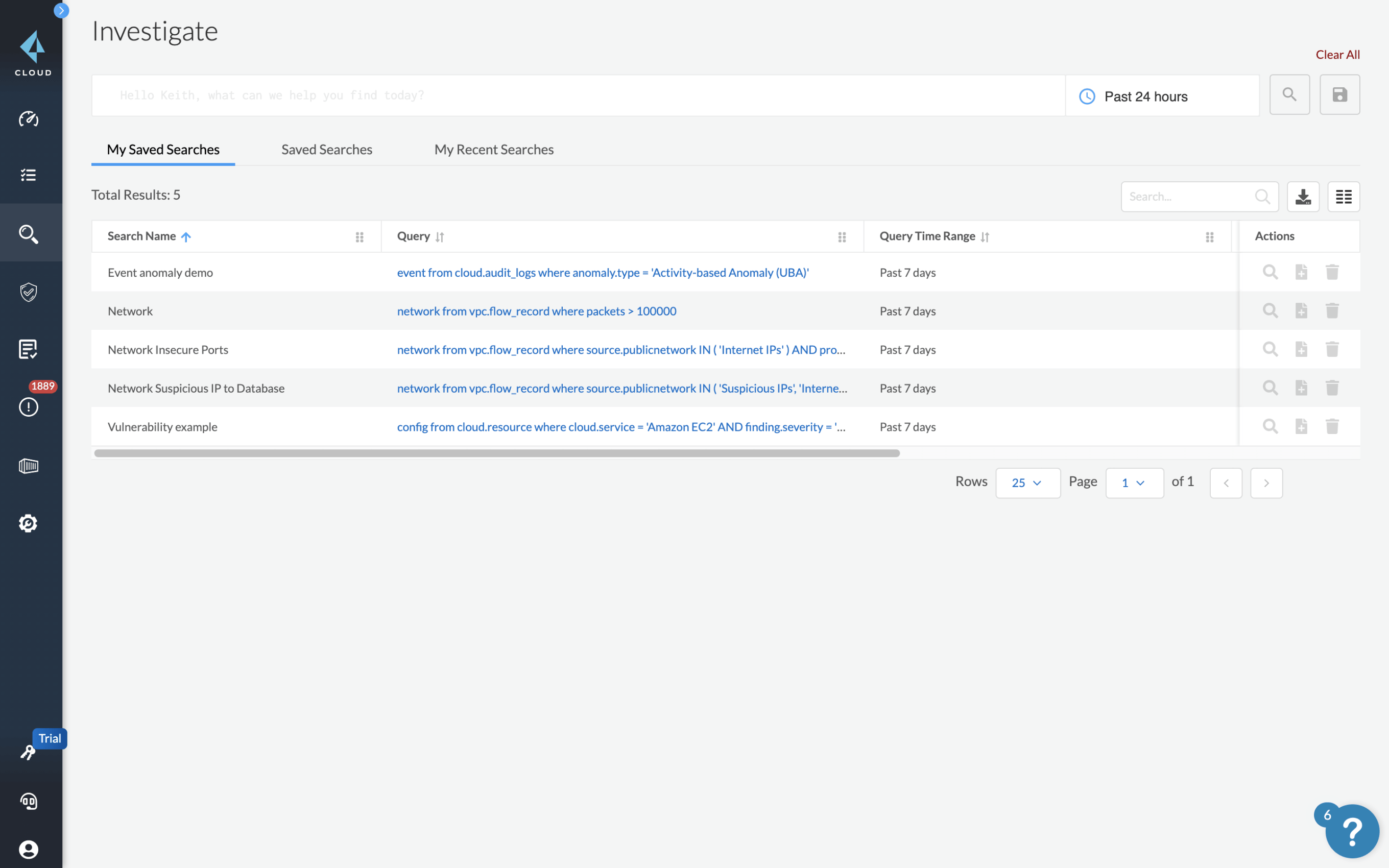
Amazon S3 Malware Scanning Using Trend Micro Cloud One and AWS Security Hub | AWS Partner Network (APN) Blog
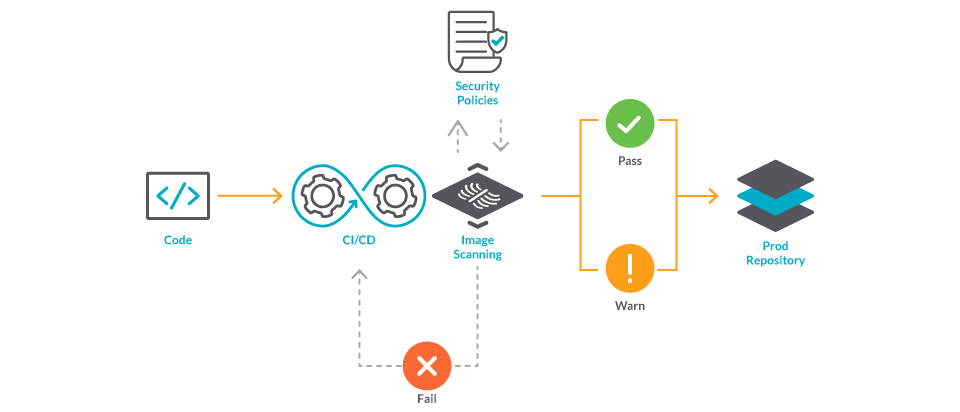
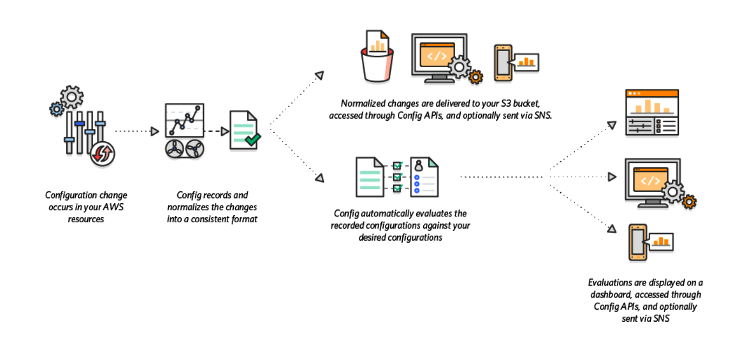
Cloud SaaS security patterns and solutions in AWS and Microsoft Azure. | Download Scientific Diagram